Introduction
In the current landscape, cryptocurrency has established itself as a valuable asset that is increasingly targeted by malicious actors. Its high liquidity and ease of transfer can present challenges for withdrawal and recovery following transactions. As a result, there has been a notable increase in scams, including both traditional schemes with a long history and new forms of fraud specifically tailored to exploit cryptocurrency technology.
In this article, we will discuss some of the most common types of cryptocurrency scams.
Social Media Giveaway Scam
Nowadays, on social media such as Twitter and Facebook, everyone They all look so generous and generous, which is incredible. If you look at the replies to popular tweets, you're bound to find that a cryptocurrency company or celebrity you like is giving away a gift. The other party will promise you: as long as you send them 1BNB/BTC/ETH, you will get 10 times the return! It seems like a pie-in-the-sky blessing, right? However, pie-in-the-sky stories are inherently unbelievable. Many of these scams can be seen through this common sense alone.
It is unlikely that any legitimate giveaway will require you to wire a sum of money first. You should be wary of such messages on social media. These accounts may look similar to accounts you're familiar with, but it's actually just a scam technique. As for the dozens of replies expressing gratitude in the comments, they were also posted through fake accounts or bots, which is a routine to implement a giveaway scam.
Suffice to say, you should completely ignore these messages. If you really think these messages are true, you can check the information introduction carefully and you will find the differences. You will soon realize that the Twitter or Facebook profile is fake.
Even if CoinCatch or any other organization holds a giveaway, you will never be asked to send money first.
Pyramid and Ponzi Schemes
Pyramid schemes and Ponzi schemes are slightly different, but overall very similar, so put them in the same category. Both types of scams above require participants to use huge profits as bait to attract downline members to continue joining.
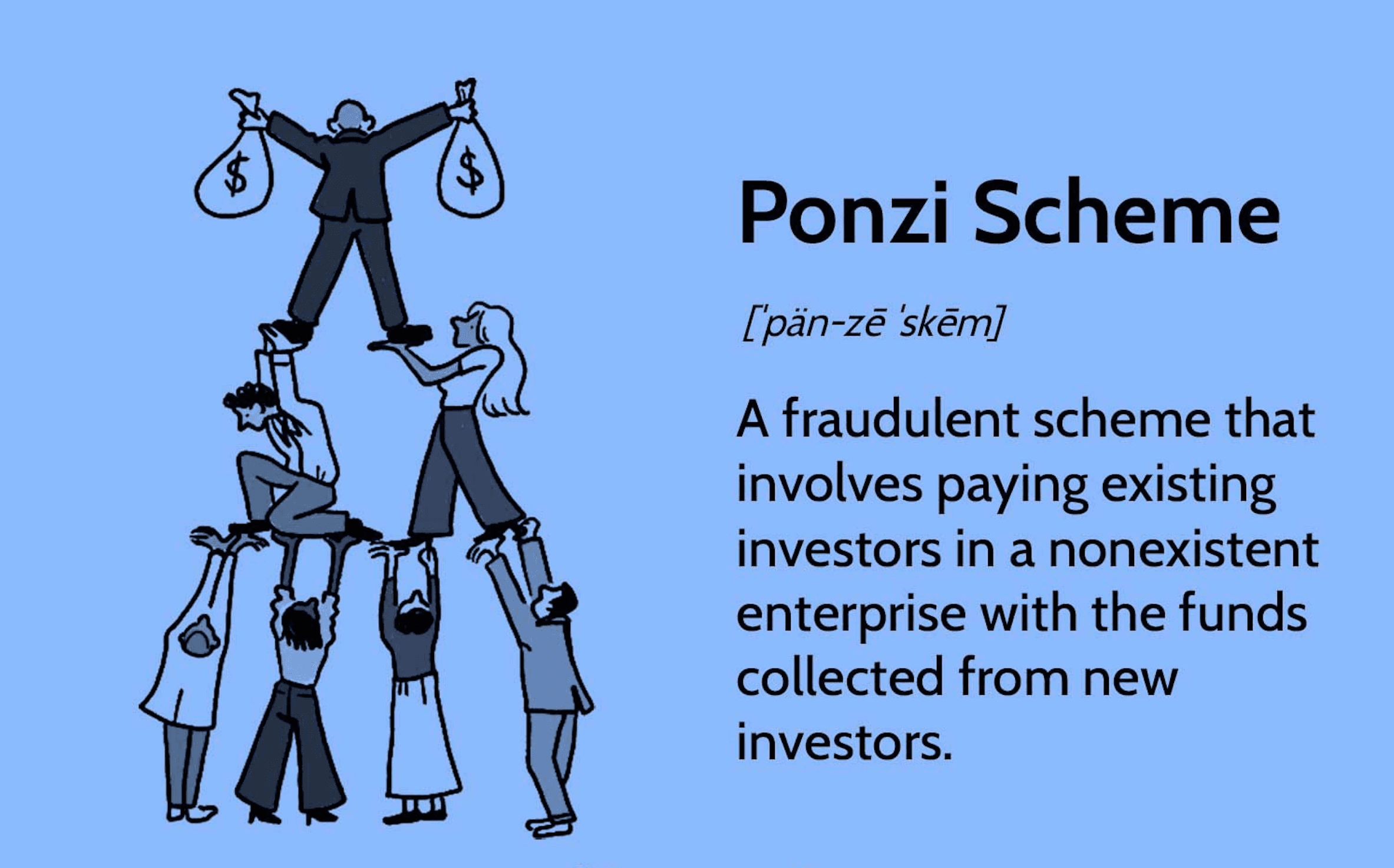
Ponzi Scheme
In a Ponzi scheme, you may hear that an investment is stable Earn (this is the first red flag!). Often, this scam will be disguised as a portfolio management service. There is no magic formula at work, and the "gains" you receive are simply other investors' money.
The organizer adds newly collected investor funds to the cash pool. Only cash inflows come from new entrants, and previous investors will receive funds from new entrants. This cycle will continue as new entrants join, and when there is no more cash to maintain investors' returns, the scam will quickly collapse.
For example, if an organization promises a 10% return on earnings within a month, after you invest $100, the organizer invites another customer to also invest $100. The manipulator uses these newfound funds to pay you $110 at the end of the month. Then he needs to attract another customer to join and pay the second customer at the same time. This cycle continues until the scam eventually falls apart.
Pyramid Schemes
In a pyramid scheme, those involved have to do more work. Organizers are at the top of the pyramid. They will recruit a certain number of people to work for them. These people will then recruit others to work for them, and they will develop layer by layer, eventually forming a huge architecture that will appear as new levels are created. Exponential growth expands (hence the name "pyramid").
Ponzi Scheme. Source: Investopedia
What we have described so far is only an organizational chart, and large ( Legal) businesses may also have such a structure. However, what is different about a pyramid scheme is that it promises to receive corresponding profits every time it recruits new members. For example: the organizer promised that Leah and Bob had the right to recruit new members at a price of US$100 each, and then receive 50% of the new members' profits. Leah and Bob can also inform the people they recruit of the same profit rules (they need to recruit at least two new members to recoup their initial investment).
For example, if Leah successfully recruits Carol and Dan as members (each worth $100), she will only earn $100 because half of her income will go to her upline. If Carol can also sell memberships, the income will increase step by step. Leah gets half of Carol's income, and the organizer gets half of Leah's income.
As the pyramid scheme continues to grow and promotion costs shift from low to high, senior members will earn more and more. However, due to rapid growth, this model cannot be sustained in the long term.
Sometimes, participants need to pay a sum of money in order to be able to sell a product or service. You may have heard of certain multi-level marketing (MLM) companies being accused of operating pyramid schemes in this manner.
Fake applications
If we are not careful enough, it is easy to ignore the information on fake applications. warning sign. Often these scams lead users to download malicious apps, some of which mimic popular apps of the day.
Once a user installs a malicious application, everything may appear to be fine, but in reality, these applications are specifically designed to steal your cryptocurrency. In crypto space, there have been many cases where users downloaded malicious applications from developers pretending to be large crypto companies.
In this case, if the user deposits or pays according to the given wallet, the money will be sent to the fraudster's address. Once the funds are transferred, there is no button to undo it.
The reason why people are fooled by these scams is also related to their APP rankings. Although malicious apps, some are also ranked very high in the Apple Store or Google Play, giving people the illusion of legitimacy. To avoid being infected by them, you should only download apps from official websites or links from reliable sources. When using the Apple Store or Google Play Store, you'll also want to check the publisher's credentials.
Phishing
Even if you are new to the field of cryptocurrency Even newbies are familiar with phishing. Phishing usually refers to criminals pretending to be relevant people or companies to contact victims and obtain their personal information and data. Phishing occurs through a variety of media, including phone calls, emails, fake websites or social messaging apps. In the field of cryptocurrency, social messaging app fraud is particularly common.
Fraudsters do not follow a set formula when trying to obtain personal information. You may receive an email informing you that there is a problem with your trading account and you need to click on a link to resolve it. This link will redirect to a fake website that looks very similar to the original website and prompt you to log in. This allows fraudsters to steal your credentials and even your passwords.
There is also a common form of Telegram fraud. Some criminals will lurk in the official groups of cryptocurrency wallets or trading platforms. When users report problems in the group, criminals will pretend to be customer service personnel or team members to contact the users privately and encourage them to share personal information and mnemonic phrases.
Knowing your mnemonic phrase gives you access to your funds. Never disclose this information to anyone, even legitimate companies, under any circumstances. Your mnemonic phrase is not required to troubleshoot wallet issues, so anyone who asks for your mnemonic phrase can be considered a scammer.
As for trading accounts, CoinCatch will never ask you for your password, as are most other services. If you receive unsolicited messages, the most prudent thing to do is not to participate and contact the company through the methods published on the official website.
Other security tips include:
-
Check the URLs of the websites you visit, scammers will often register a company that looks very similar to the real company (e.g.
coincatch.com) Similar domain names.
-
Bookmark domains you visit frequently, as search engines may display malicious code in error.
-
If you have any questions about the information you received, please ignore the email and contact the merchant or customer service through official channels.
-
No one needs to have access to your private key or mnemonic phrase.
Vested interests
The abbreviation of DYOR (Do Your Own Research, do your own research) Words is a concept often mentioned in the field of cryptocurrency, and they are very reasonable.
Before investing real money in digital currencies or tokens, you should analyze and make decisions rationally and not blindly trust other people’s advice. You can never be sure of someone else's true motives. The reason why they vigorously promote an initial coin offering (ICO) project may be because they receive a commission or they have invested a large amount of money themselves. Whether it is a random stranger or an influential celebrity, this problem will exist. No project can guarantee a guaranteed profit without loss. In fact, most projects fail.
To objectively evaluate a project, you should consider a variety of factors. Everyone has their own way of researching potential investments. Here are some questions to ask when getting started:
-
How are currencies/tokens distributed?
-
Is most of the supply concentrated in the hands of a few users?
-
What is the unique selling point of this project?
-
What other projects are doing the same thing, and how does this project compare?
-
Who is responsible for the project? Does the team have a good credit history?
-
What is the community like for this project? What product is being built?
-
Does the world really need this currency/token?
Summary
There are numerous malicious actors attempting to exploit unsuspecting cryptocurrency users through various schemes. To protect yourself from common scams, it is important to remain vigilant and aware of the tactics employed. Always verify that you are using the official website or app. Remember: If an investment opportunity seems too good to be true, it likely warrants further scrutiny.