In the evolving landscape of cryptocurrency and decentralized networks, Sybil attacks have emerged as a significant threat to network integrity and security. Just recently, on September 16, 2025, blockchain analytics firm Bubblemaps reported that a single entity profited approximately $4 million from the
AVNT airdrop
through what appeared to be a coordinated Sybil attack spread across more than 300 addresses. This incident followed similar patterns observed in earlier attacks, including the
MYX Finance scandal
where $170 million in tokens were allegedly diverted to suspicious wallets. These attacks highlight the ongoing vulnerability of decentralized systems to identity manipulation and the continuous need for effective detection and prevention mechanisms.
The term "Sybil attack" originates from the case study of a woman with
multiple personality
disorder
named
Sybil Dorsett . In cybersecurity contexts, it refers to a scenario where a single entity controls multiple fake identities to gain disproportionate influence over a network. This article explores the definition, characteristics, real-world cases, detection methods, and preventive measures against Sybil attacks in cryptocurrency ecosystems.
What is a Sybil Attack?
A Sybil attack is a type of
security threat in which an attacker creates and controls multiple false identities within a network system. These fabricated identities appear to be independent legitimate participants but are actually controlled by a single malicious entity. The primary goal of such attacks is to undermine the trust and functionality of decentralized systems by gaining excessive influence over decision-making processes, consensus mechanisms, or resource allocation.
The concept was first introduced by John Douceur in 2002 in the context of peer-to-peer networks, where he demonstrated that such attacks could effectively compromise distributed systems that rely on redundancy and majority voting . The name "Sybil" was drawn from the famous case of Sybil Dorsett, a woman diagnosed with multiple personality disorder, metaphorically representing one entity possessing multiple identities.
In cryptocurrency networks, Sybil attacks are particularly concerning because blockchain technology fundamentally relies on decentralized consensus and the assumption that most participants are honest and independent. When an attacker successfully controls numerous fake nodes or identities, they can potentially manipulate transaction validation, disrupt consensus formation, and even reverse confirmed transactions.
Table: Types of Sybil Attacks in Cryptocurrency Networks
| Attack Type |
Description |
Common Targets |
| Direct Communication |
Sybil nodes communicate directly with legitimate nodes |
Peer-to-peer networks, node consensus |
| Indirect Communication |
Malicious nodes claim to route messages to Sybil nodes |
Distributed systems, relay networks |
| Identity Forgery |
Attacker creates arbitrary identities for Sybil nodes |
Permissionless networks, airdrops |
| Identity Theft |
Attacker hijacks legitimate identities for Sybil nodes |
Networks with limited identity namespace |
| Simultaneous Attack |
All Sybil identities participate concurrently in the network |
Voting systems, consensus mechanisms |
| Non-Simultaneous Attack |
Sybil identities appear and disappear at different times |
Long-term reputation systems |
Key Characteristics of Sybil Attacks
Sybil attacks in cryptocurrency environments typically exhibit several
distinct patterns and characteristics that can help identify them. According to the recent Bubblemaps report on the AVNT airdrop incident, some telltale signs include:
Common Funding Sources: The fraudulent addresses often receive initial funding from the same exchange or source. In the AVNT case, multiple addresses received their initial funds from Coinbase, suggesting coordinated preparation for the attack.
Similar Transaction Patterns: The addresses typically show identical or highly similar transaction histories. For instance, in the MYX Finance case, 100 addresses received identical deposits from the OKX exchange on the same day (April 19, 2025), just before the airdrop announcement.
Dormancy Periods: Many Sybil addresses remain dormant until the critical moment (e.g., an airdrop or governance vote). The MYX-related wallets showed no activity prior to claiming their tokens on May 7, 2025.
Synchronized Actions: The addresses often perform actions in highly coordinated ways, such as claiming airdrops simultaneously or executing similar smart contract interactions within a short time frame.
Rapid Consolidation: After obtaining rewards or tokens, the funds are quickly funneled to a few destination addresses, often followed by transfers to centralized exchanges like Bybit or Gate for liquidation.
These behavioral patterns create anomalies in the network data that can be detected through sophisticated
blockchain analysis and clustering algorithms. The increasing professionalism of these attacks makes them harder to detect, as attackers continually refine their methods to avoid obvious patterns.
Notable Sybil Attack Cases in Cryptocurrency
The MYX Finance $170 Million Airdrop Scandal
The
$MYX
team is alleged to have directly tied to wallets that claimed $170M from their airdrop. Source: Bubblemaps X account
In what experts have called one of the
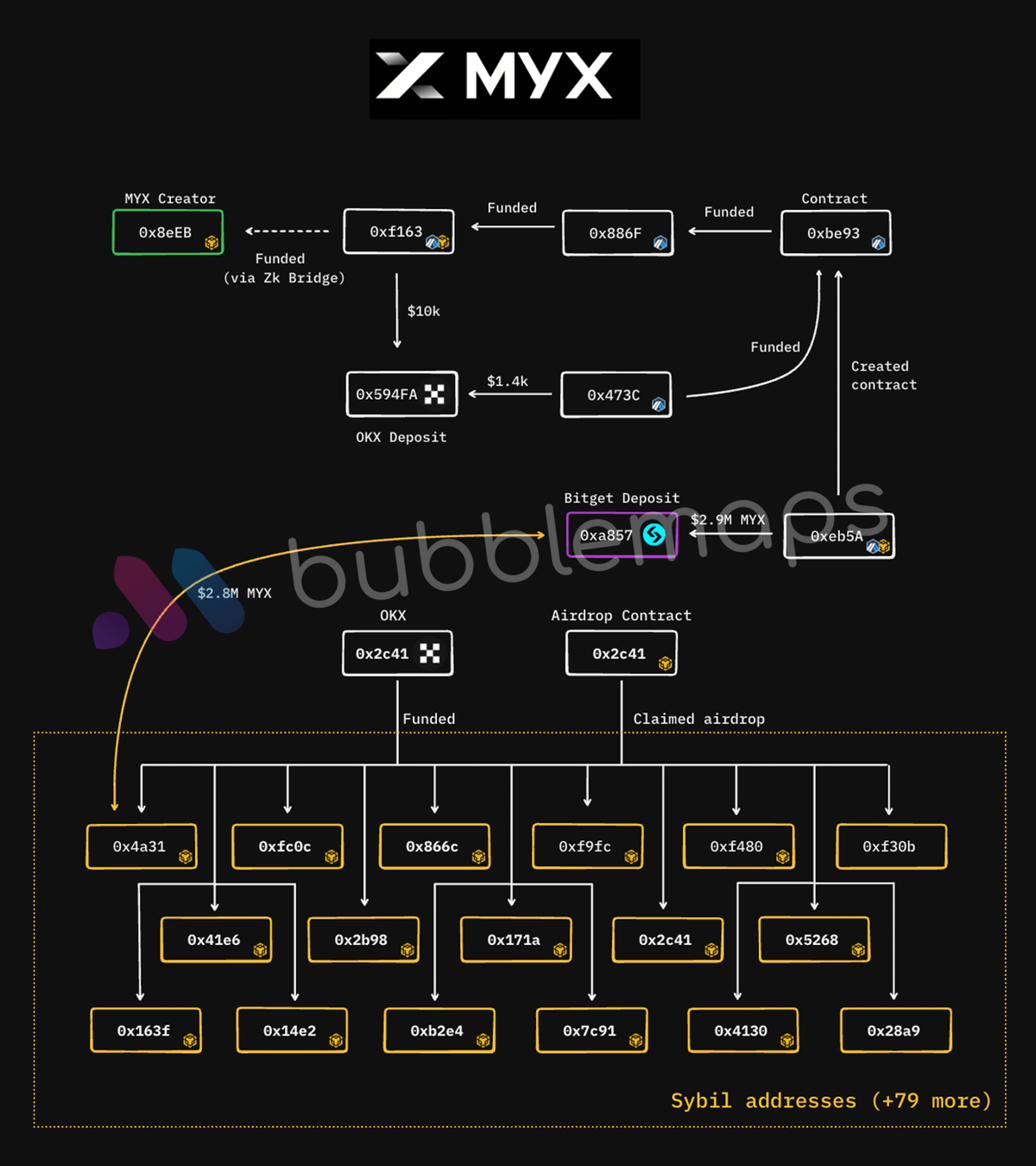
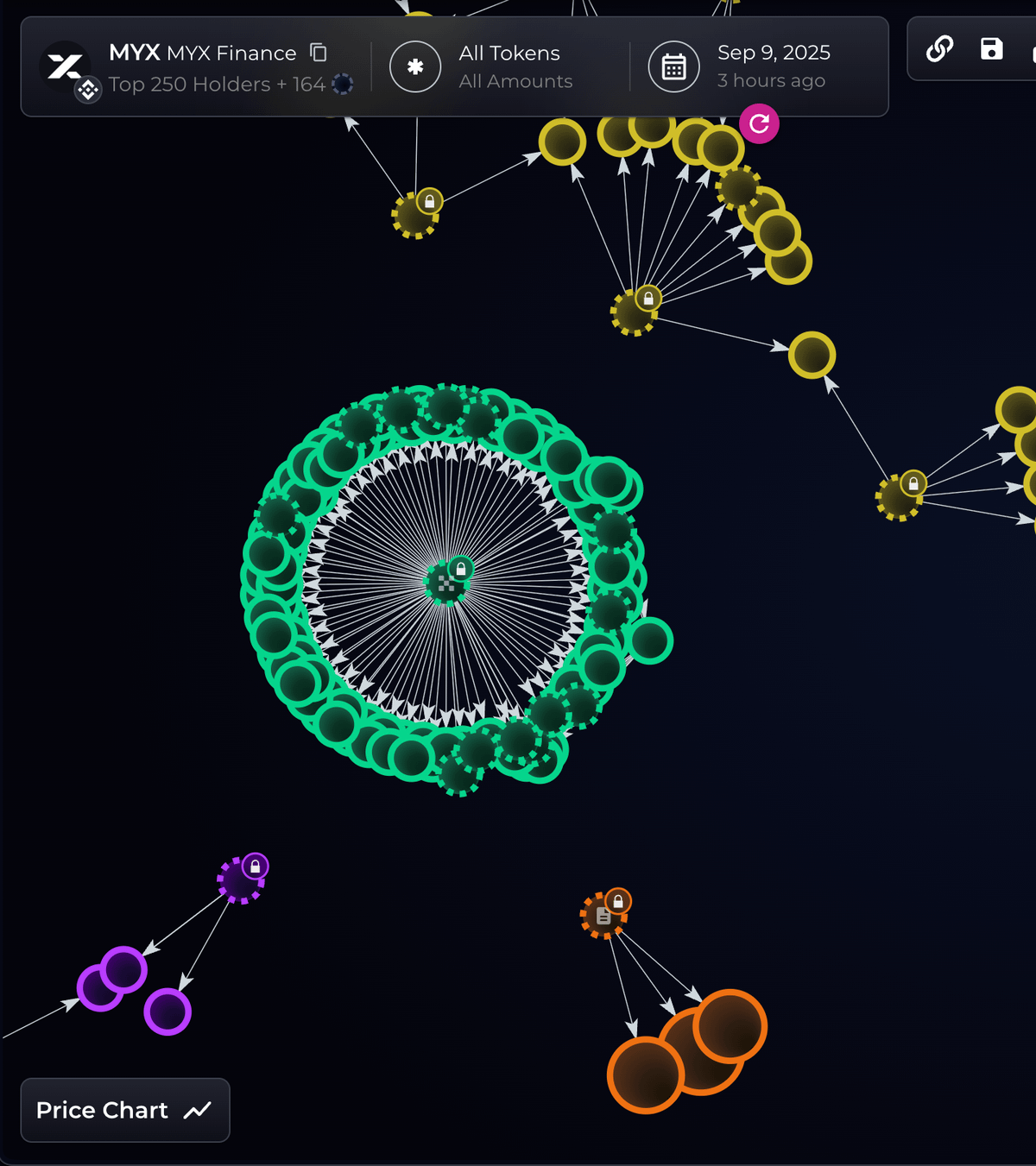
largest suspected Sybil attacks in crypto history, MYX Finance faced allegations in September 2025 that its team was linked to a cluster of wallets that received $170 million during the project's airdrop . Analytics experts from Bubble Maps discovered that 100 addresses received identical deposits from the OKX exchange on April 19, 2025, just before the airdrop announcement. These wallets showed no activity prior to claiming their tokens on May 7 and together secured 9.8 million MYX tokens, then valued at $170 million.
Most notably, Bubble Maps traced cryptographic connections between one of these wallets and the known address of MYX Finance's founder. Transactions linked the founder's address (0x8eEB) to another account in the cluster, which followed the same pattern as 95 other suspected Sybil wallets. One of the addresses even sent $2.8 million in tokens to another wallet identified as belonging to the founder.
The MYX Finance team issued a response denying the accusations, claiming that most wallets received "fair compensation for real participation," while some larger holders had simply requested address changes before the airdrop. However, Bubble Maps called the explanation "vague" and demanded clearer answers about coordinated wallet behavior.
Monero's Privacy Network Attack (2020)
In November 2020, the
privacy-focused cryptocurrency Monero suffered a Sybil attack that lasted for approximately 10 days . The attacker created numerous malicious nodes in an attempt to break the network's privacy features by tracing transactions and identifying users. Although the attack was eventually detected and mitigated, it highlighted the vulnerability of even well-established cryptocurrencies to Sybil attacks, especially those prioritizing privacy and anonymity.
Tor Network Relays Incident (2014)
While not exclusively a cryptocurrency incident, the 2014 Tor Network Sybil attack had significant implications for cryptocurrency users who relied on Tor for
transaction privacy . Researchers discovered that malicious actors had been operating a large number of Tor relays, potentially allowing them to de-anonymize users and their activities. This case highlighted the importance of Sybil resistance beyond blockchain networks, extending to all decentralized systems relying on distributed trust.
Table: Major Sybil Attack Cases in Cryptocurrency (2014-2025)
| Year |
Target |
Method |
Impact |
| 2014 |
Tor Network |
Malicious relay nodes |
Potential de-anonymization of users |
| 2020 |
Monero Network |
Fake nodes targeting privacy |
Attempted transaction tracing |
| 2025 |
MYX Finance |
100 fake wallet addresses |
$170 million in airdrop tokens |
| 2025 |
AVNT Network |
300+ coordinated addresses |
$4 million in airdrop tokens |
How Sybil Attacks Are Monitored and Detected
Detecting Sybil attacks requires
sophisticated analysis of on-chain data and network behavior patterns. Analytics firms like Bubble Maps employ specialized techniques to identify suspicious clustering and coordination among addresses:
Transaction Graph Analysis: By mapping transactions between addresses, analysts can identify
common funding sources and destination addresses. Clusters of addresses that receive identical amounts from the same source within a short time frame often indicate Sybil behavior.
Timing Pattern Recognition: Sybil operations often show
unnatural synchronization in their activities. Detection algorithms look for addresses that perform actions simultaneously or in predictable sequences, which is uncommon among organic users.
Behavioral Analysis: Legitimate users typically exhibit varied interaction patterns with protocols, while Sybil addresses often show
identical or nearly identical behavior sequences, such as performing the same actions in the same order.
Network Analysis: In addition to on-chain data, analysts may examine
network-level information such as IP addresses, geolocation data, and node connection patterns to identify potentially malicious clusters.
Machine Learning Approaches: Advanced detection systems employ
machine learning algorithms strained on known Sybil patterns to identify suspicious address clusters with high accuracy. These systems can adapt to evolving attack methods over time.
The Bubblemaps report on the AVNT airdrop demonstrated how these techniques work in practice: by identifying addresses that received funds from Coinbase, engaged in similar swapping activities on Avantis, claimed airdrops simultaneously, and finally consolidated funds to a few addresses before transferring to centralized exchanges.
Prevention and Resistance Measures Against Sybil Attacks
Various
defense mechanisms have been developed to protect cryptocurrency networks against Sybil attacks. These approaches make it economically impractical or computationally infeasible for an attacker to control multiple identities:
Consensus-Based Resistance: Many blockchains implement consensus algorithms that inherently
discourage Sybilattacks by requiring significant resource investment:
-
Proof of Work (PoW): Used by Bitcoin and others, requires computational effort to participate in consensus, making identity creation expensive.
-
Proof of Stake (PoS): Requires participants to hold and "stake" cryptocurrency, making control of the network economically prohibitive.
-
Delegated Proof of Stake (DPoS): Stakeholders vote for block producers, adding a layer of reputation to the staking mechanism.
Economic Incentives: Designing systems that make Sybil attacks
finally unviable by requiring substantial economic commitments that would be lost if malicious behavior is detected.
Identity Verification: While contrary to the pseudonymous nature of many cryptocurrencies, some applications require
identity verification for participation in governance or airdrops. This can be implemented through various zero-knowledge proof systems to balance privacy and security.
Reputation Systems: Implementing
long-term reputation metrics that develop over time based on consistent participant behavior makes it difficult for newly created Sybil identities to gain influence immediately.
Community Governance: Some projects, like LayerZero, have adopted
community-based detection methods, inviting users to "hunt" suspected Sybil actors and rewarding them with a share of the reclaimed tokens.
Technical Solutions: Wireless networks have developed specialized detection methods using
hardware fingerprintslike signal frequency offset distribution or angle of arrival (AoA) estimation to identify devices creating multiple identities. While not directly applicable to blockchain, similar principle-based approaches can be adapted for cryptocurrency networks.
The effectiveness of any single approach is limited, so most modern blockchain projects implement
multiple layers of Sybil resistance appropriate to their specific use cases and security requirements.
Conclusion and Future Outlook
Sybil attacks remain a persistent threat to cryptocurrency networks and decentralized systems more broadly. As the recent AVNT and MYX Finance incidents demonstrate, these attacks are becoming more sophisticated and economically significant, with potential rewards amounting to millions of dollars . The continuous evolution of detection methods is matched by increasingly sophisticated evasion techniques, creating an ongoing arms race between attackers and defenders.
The future of Sybil resistance likely lies in adaptive multi-layered approaches that combine economic barriers, consensus mechanisms, behavioral analysis, and community governance. As blockchain analytics tools become more advanced, they will likely be able to detect increasingly subtle patterns of Sybil behavior while preserving user privacy and decentralization principles.
For cryptocurrency projects designing airdrops or governance systems, implementing Sybil-resistant mechanisms from the outset is crucial. This may include address screening, gradual reward distribution, stake-based participation requirements, and ongoing monitoring for suspicious patterns. Users should also educate themselves about these threats and support projects that take Sybil resistance seriously.
While completely eliminating Sybil attacks may be impossible, making them economically unfeasible and technically challenging can protect the integrity of decentralized networks and maintain trust in cryptocurrency ecosystems. Continued research and development in Sybil detection and prevention will be essential as blockchain technology evolves and expands into new applications.
Reference:
Journal of Information Engineering University. (2020). Detection of Sybil Attacks Based on Frequency Offset Distribution in WLAN. 21(3), 290-296.
CoinCatch Team
Disclaimer:
Digital asset prices carry high market risk and price volatility. You should carefully consider your investment experience, financial situation, investment objectives, and risk tolerance. CoinCatch is not responsible for any losses that may occur. This article should not be considered financial advice.